- published
- reading time
- 10 minutes
: :
–┼──────────────────────────────────────────────────────────────────────┼–
+–─┘ └─–+
Adware Digital Pulse pt.1
: : : :
┌─|────────────────────────────────────────────────────────────────────────|─┐
└─│──┐– –────────────────────────────────────────────────────────────– –┌──│─┘
┌─┘ | | └─┐
│: : : :│
: :
–┼──────────────────────────────────────────────────────────────────────┼–
+–─┘ └─–+
Adware Digital Pulse pt.1
: : : :
┌─|────────────────────────────────────────────────────────────────────────|─┐
└─│──┐– –────────────────────────────────────────────────────────────– –┌──│─┘
┌─┘ | | └─┐
│: : : :│
Table of Contents
Intro
Greetings! Today, I’ll start a series of malware analysis posts. In this type of post, I’ll present a series of known types of malicious files to analyze and disseminate more knowledge about cyber threats. This is a static analysis. We discussed the reversing workflow in Radare2 vs Ghidra right before the conclusion section.
I’m using (mainly) macOS and Ubuntu in an isolated virtual machine for conducting the analysis. This means the virtual machine operates with isolated disk space and a disabled network.
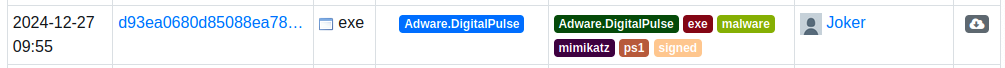
For collecting malware samples, Malware Bazaar1 is my source. I go there and, through the tags, collect malware that I think is worth analyzing. The software we will work on today is an adware sample, posted by Joker.
Our Static Analisys can be splited in three main parts:
- Threat Intelligence platforms
- Assets Analisys
- Code flow Analisys
Threat Intelligence platforms
First things first: we can extract information from executables without even “touching” them by using Threat Intelligence platforms. While this can be done manually, for practicality, we will consult a few databases using malwoverview2, created by Alexandre Borges. Since we are working in the terminal, centralizing logs is helpful for providing a panoramic overview of pre-analysis information that can lead to a cleaner and more objective investigation.
malwoverview -v 2 -V <sha256 hash> -o 0 (Virus Total)
malwoverview -a 5 -A <sha256 hash> -o 0 (Hybrid-Analysis)
malwoverview -n 4 -N <sha256 hash> -o 0 (Alien Vault)
malwoverview -b 1 -B <sha256 hash> -o 0 (Malware Bazaar)
malwoverview -x 1 -X <sha256 hash> -o 0 (Triage)
malwoverview -x 2 -X <triage_id> -o 0 (Triage)
These are the databases we consulted, and we already have some interesting findings in the logs:
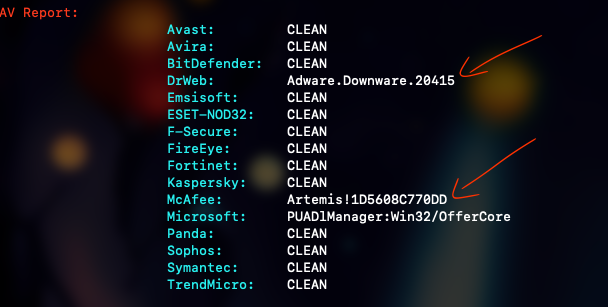
According to these threat sources, we are dealing with malicious adware. Adware is a type of software designed to display advertisements on a user’s device, typically through pop-ups, banners, or embedded ads in applications or web browsers.
Types of Adware:
-
Legitimate Adware: Some adware is intentionally installed by users as part of free software supported by ads.
-
Malicious Adware: This type operates without consent and may include spyware-like features that collect personal information or compromise device security.
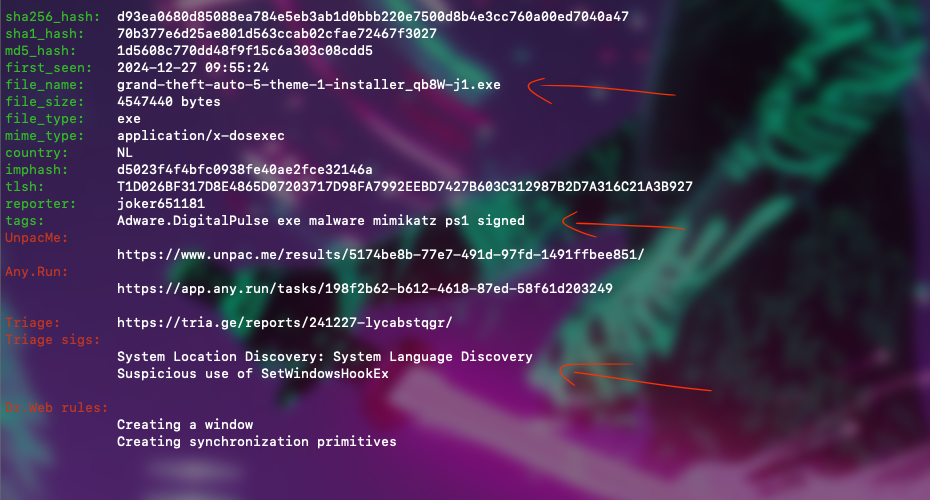
Despite strong evidence such as “Suspicious use of SetWindowsHookEx” and similar indicators, one detail that caught my attention is the name of the file: grand-theft-auto-5-theme-1-installer_qb8W-j1.exe. It is very common for malicious software to disguise itself as game-related files since they need to be attractive to spread widely. Recreational activities often have this scalability feature.
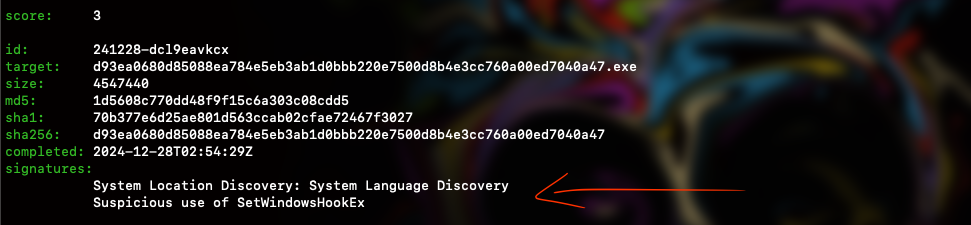
We can also see that one of the triggers suggests the file might be part of DigitalPulse’s family. The file appears to be digitally signed and shows indications of attempting to gather information about the system’s location via language settings. Furthermore, the presence of a Mimikatz-related3 signature suggests it may attempt to steal credentials or other host information. Lastly, there’s the presence of SetWindowsHookEx, which is a Windows API function that can be used legitimately but seems suspicious in this context.
SetWindowsHookEx is a Windows API function that allows programs to install hook procedures to monitor system events such as keyboard input, mouse clicks, and window messages. To understand better how it works, you can refer to Microsoft’s documentation4.
What is a Digital Pulse adware?
- Stealthy Installation: Digital Pulse is typically bundled with cracked software and games, installing silently in the background.
- Proxy Functionality: Once installed, it turns the infected device into a residential exit node for a proxy network.
- Evasion Techniques: The malware is digitally signed, allowing it to evade antivirus detection.
- Persistence Mechanisms: It creates registry keys and scheduled tasks to ensure it runs on system boot.
Assets Analysis
We will touch on it to test the waters. Checking some file sections can be very revealing.
Headers analysis
Ok, let’s display the file’s header info:
objdump -f FILE_NAME
The coff-i386 file format refers to the Common Object File Format (COFF) for Intel 386 architectures. This is a specific variant the COFF format used for object file and executables on x86 systems. While largely replaced by ELF on Unix-like systems, COFF variants are still used in some contexts, including Microsoft Windows (as part of the PE format) and some embedded systems.
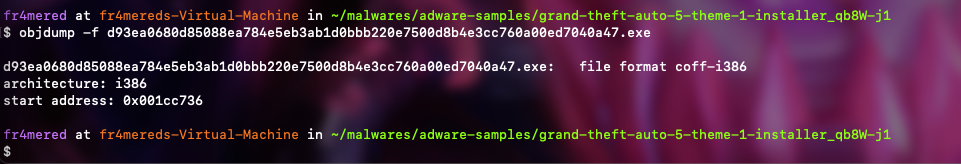
Display program headers & Display dynamic section:
objdump -p FILE_NAME
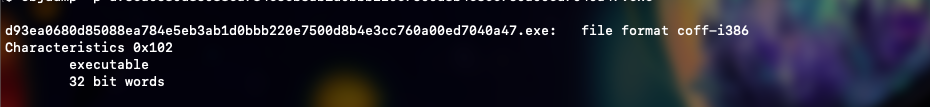
The characteristics field is a bitmask that describes attributes of the executable file. In our sample we have:
- 0x02:
IMAGE_FILE_EXECUTABLE_IMAGE - 0x100:
IMAGE_FILE_32BIT_MACHINE
From the PE file header we are capable to check some features which are according to the tags from the databases that we collected like:
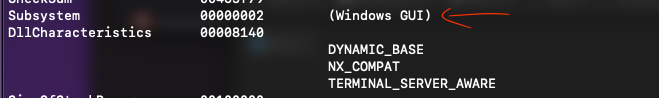
DLLCharacteristics are flags in the PE file format that describe various attributes and behaviors of a Dynamic-Link Library (DLL) or executable. These characteristics provide information to the operating system about how to handle and execute the file. Some important DLLCharacteristics include:
-
DYNAMIC_BASE: Indicates the image can be relocated at load time (ASLR support). -
NX_COMPAT: The image is compatible with Data Execution Prevention (DEP). -
TERMINAL_SERVER_AWARE: The application is aware of Terminal Services environment. The file does support Windows GUI, which means that it must have some interface but also presentTERMINAL_SERVER_AWARE.
The Data Directory is a component which maps important data structures within the executable file. It contains entries of every section and every entry consists of a Virtual Address and a size:
Common entries include:
• Export Table: Functions exported by the module
• Import Table: Functions imported from other modules
• Resource Table: Resources like icons and dialogs
• Exception Table: Information for structured exception handling
• Security Table: Digital signature information
• Relocation Table: Information for relocating the image
• Debug Data: Debugging information
• TLS Table: Thread Local Storage data
• Import Address Table (IAT): Addresses of imported functions
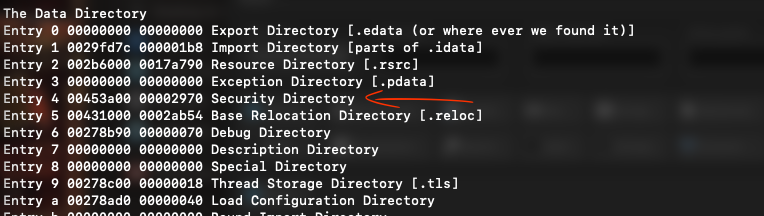
For instance, in our example, we can see that the security entry has some content in it, which suggests that the malware has a high probability of being digitally signed to bypass security checks. Additionally, we notice the presence of a TLS table section, indicating that the executable is designed for multi-threaded operation. The Thread Local Storage (TLS) table provides information about thread-specific data.

The load configuration tells us relevant information about how the executable should be loaded and executed. In particular, it has a significant number of exception handlers (1291 Structured Exception Handling (SEH) entries), which may suggest complex exception handling or possibly obfuscation techniques.
How do obfuscation techniques implies on SEH entries number?
An increased number of exceptions affects the size of exception entries. In some samples, this may be suspicious due to exception-based obfuscation methods being employed.
Summary of obfuscation techniques impacting SEH entries:
- Exception-based obfuscation: Introduces intentional exceptions throughout the code, increasing SEH count.
- Control flow obfuscation: Uses exceptions for program flow, requiring more SEH entries.
- Anti-debugging: Employs exceptions to detect debuggers, adding SEH entries.
- Code fragmentation: Breaks code into smaller, exception-protected fragments, increasing SEH count.
- Dummy handlers: Inserts fake exception handlers to confuse analysis, inflating SEH numbers
Section Analysis
The way the file stores its variables for linkage and management can be listed using objdump as well. It is very interesting, at least, to check what type of data you might encounter in each of these sections.
objdump -x FILE_NAME
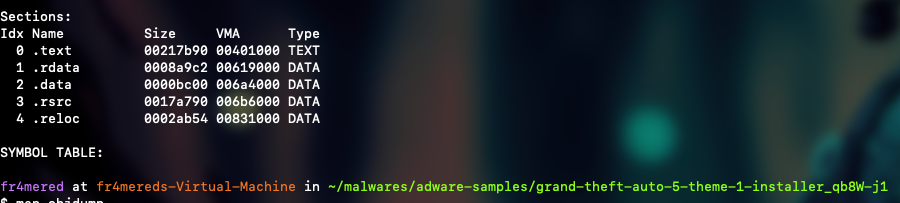
Now that we know which sections the file contains, we can go through them and see whether we find anything interesting:
strings -a -n200 FILE_NAME
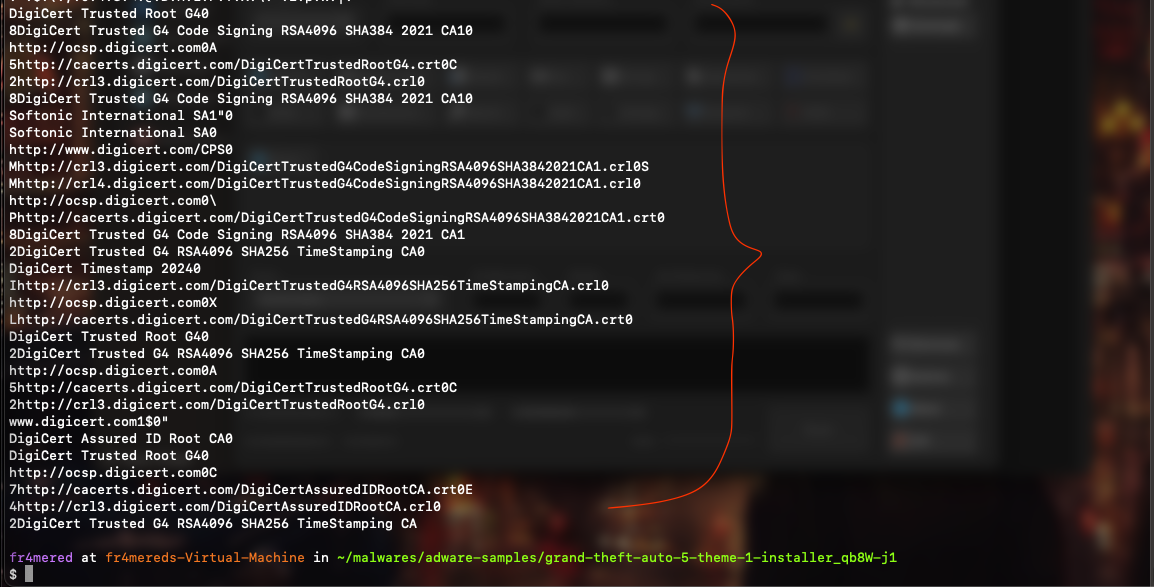

As you can see, we can identify some URL strings that reveal certificates. This suggests that although the file is supposed to be adware, there are references to certifications within it. This could be a strong indicator of digital signature obfuscation. To delve deeper into specific sections of the file, we use the following commands:
objdump -s -j .rdata FILE_NAME | head -32
objdump -s -j .text FILE_NAME
objdump -s -j .rsrc FILE_NAME
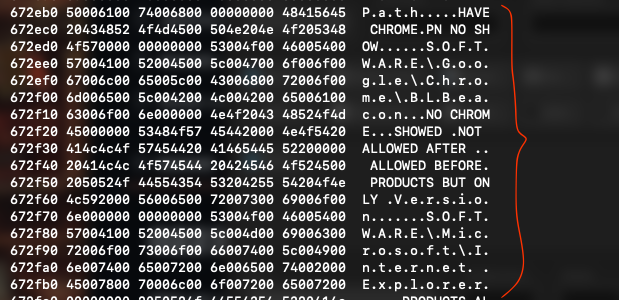
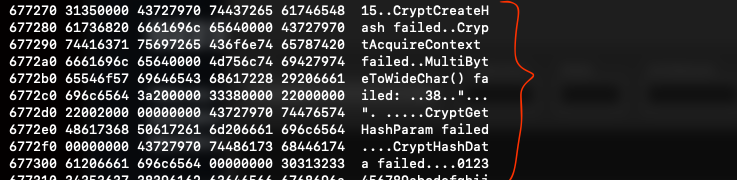
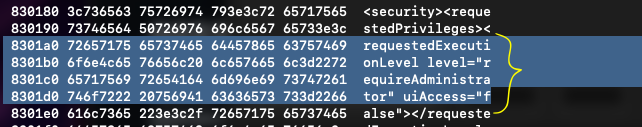
So far, we have gathered enough clues to conclude that this file is not a normal one. Why would a GTA5 theme request Administrator level access and utilize Crypt functions? Within this context, we also observe browser version-checking messages, which provide further evidence about this file’s intentions.
Entropy
Our next step is to check the file’s entropy and randomness. For this, we’ll use the ent tool.
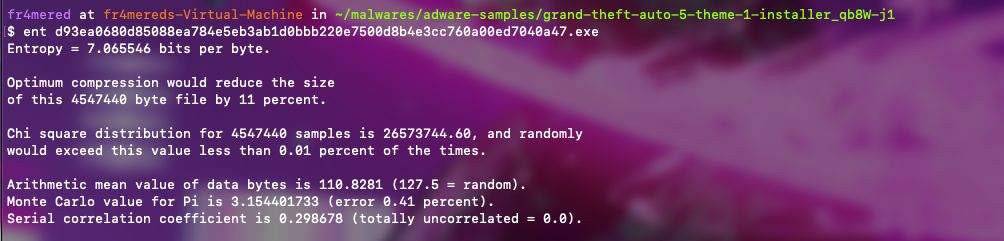
The tool provides metrics detailing entropy and other statistical properties, which help determine whether the file contains random, compressed, or encrypted content. Based on this analysis, we can observe the following:
- A measure of randomness in the file’s data.
- Low entropy (< 5): Indicates structured or plain data.
- High entropy (> 7): Suggests compressed or encrypted data.
Consequently, the metrics indicate that our file exhibits a significant increase in encryption and randomness within its data. This suggests that the function signatures we observed earlier were not merely present but actively applied. This could represent potential obfuscation or hidden payloads due to encryption or compression.
Signatures
Using signsrch5, we can observe the presence of method signatures that further reinforce our suspicions. Of course, some of these functions can be used for legitimate purposes, but given the circumstances, it is reasonable to highlight suspicious behaviors associated with these methods:
./signsrch -e file.exe
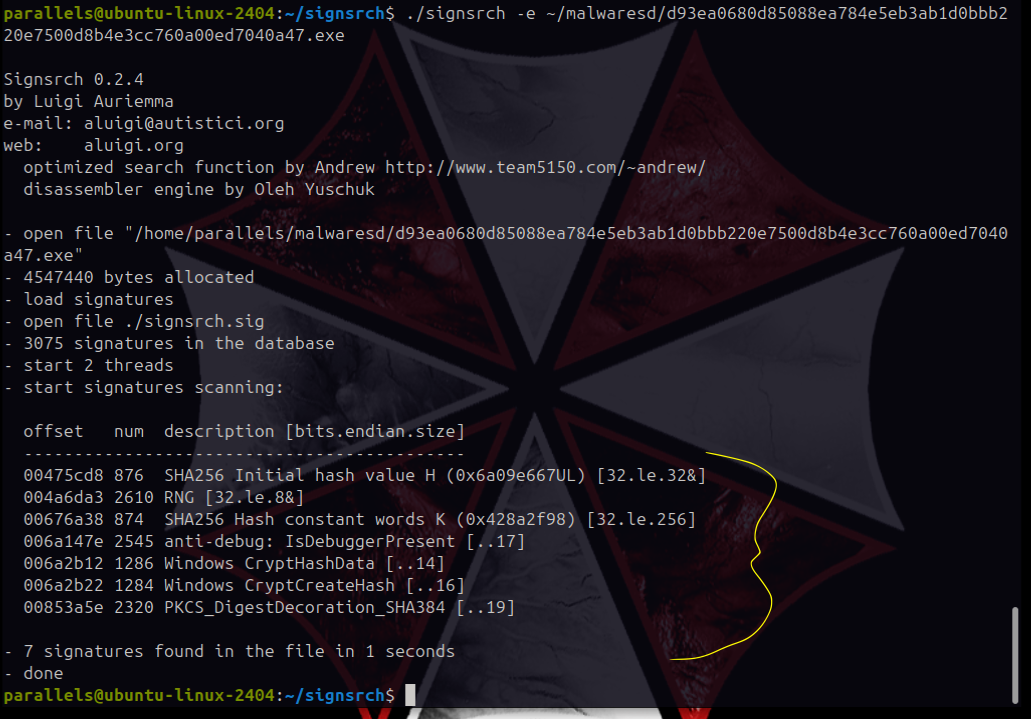
SHA256 Initial Hash Value and Hash Constant Words K
- Used for generating unique identifiers for files or data
- Can help evade detection by creating different hashes for slightly modified malware versions
RNG (Random Number Generation)
- Create unpredictable encryption keys
- Generate unique identifiers
- Assist in evading detection by introducing randomness
Anti-debug: IsDebuggerPresent
The Windows API call is used to detect if a debugger is present, and this is the most suspicious function signature:
- Helps malware evade analysis by altering behavior when being debugged.
- Can make reverse engineering more difficult
Windows CryptHashData and CryptCreateHash
These Windows cryptographic API functions are used for:
- Generating hash values of data
- Creating secure communication channels
- Potentially obfuscating malicious activities
PKCS_DigestDecoration_SHA384
- Used in digital signatures and data integrity checks
- May be employed for secure communication or evading detection
Given that we are analyzing a possible variant of Digital Pulse adware, these signatures suggest:
- Attempts to evade detection and reverse engineering
- Possible use of encryption for communication or data obfuscation
- Efforts to generate unique identifiers or signatures for the malware
Capa6
Capa is a very useful tool for reverse engineers, it collects strings and functions signatures and matches with known standard capabilities of malwares in general. It is important because is a one more filter for a possible signature that we probably missed.
./capa FILE_NAME
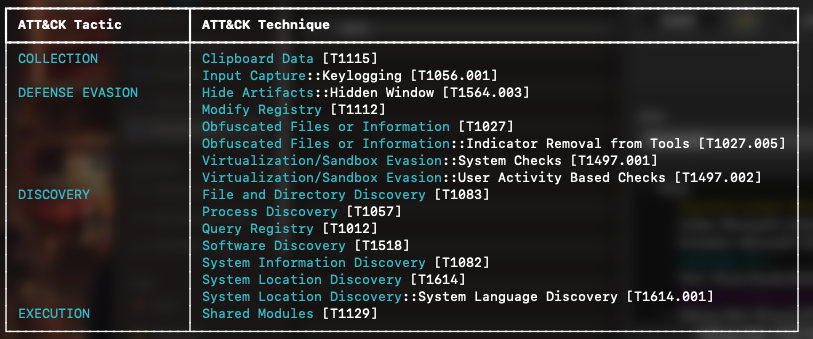
For example, in the image above, we see several attack tactics that might represent possible attack approaches. This provides a holistic overview of the malware’s suspicious behavior. In the next figure, we delve into more specific behaviors that build on this broader map.
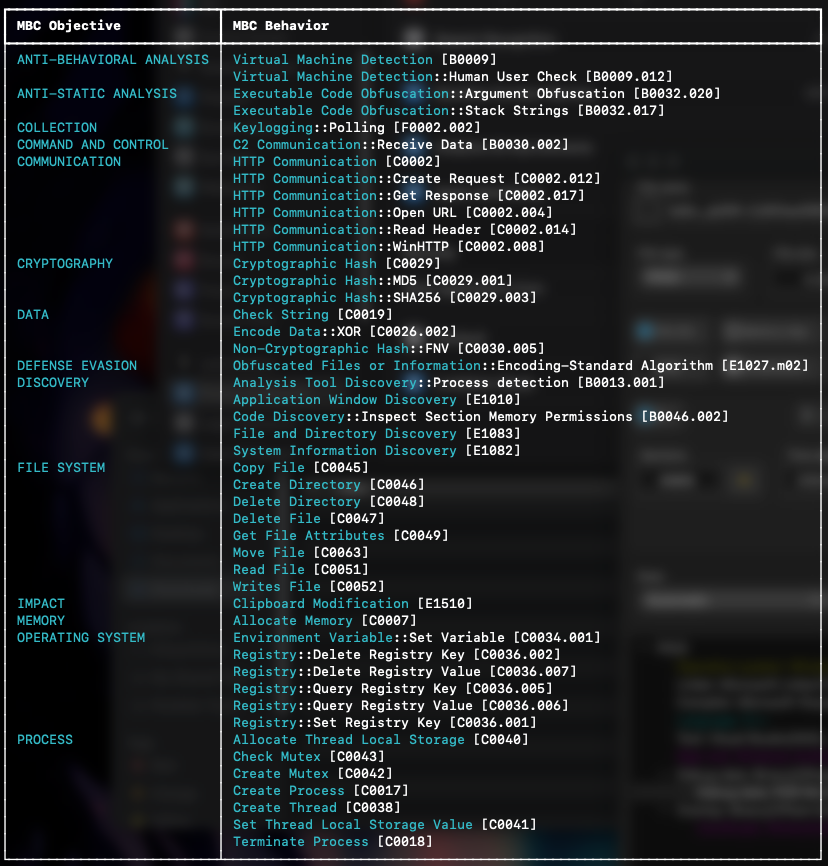
The table above is based on the Malware Behavior Catalog (MBC). If you don’t fully trust this output, you can verify it yourself. Using this information, we can analyze the code’s strings based on the MBC table to search for behaviors related to these findings:
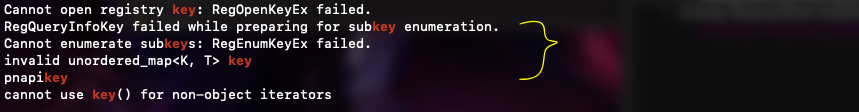
strings FILE_NAME | grep key
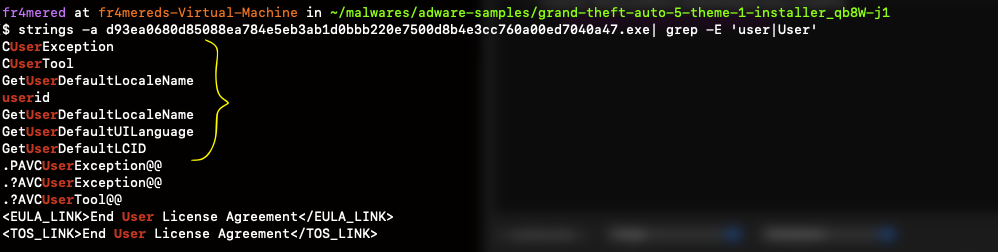
strings FILE_NAME | grep -E 'user|User'
Overview
Ok then, we will continue the Code flow Analisys on pt.2. Lets state bullet points of our potential findings in order to track the file’s behavior:
Key Findings
- Leveraging popular software themes to attract users
- Digitally signed to bypass security checks
- Obfuscation methods, such as exception-based techniques
- Employs APIs like
SetWindowsHookExfor monitoring system events - Cryptographic functions (
CryptHashData,CryptCreateHash) - High Entropy Levels
- Tracks user browsing habits, search queries, and potentially sensitive information
- Turns infected devices into residential exit nodes for proxy networks
- Establishes connections with remote servers for updates or instructions
In this first part of the malware analysis series, we conducted a static analysis of an adware sample disguised as a GTA5 theme installer. The analysis revealed techniques used by the malware to evade detection, persist on infected systems, and potentially compromise user data.
In Part 2, we will dive deeper into the Code Flow Analysis to trace the file’s behavior in detail and uncover additional insights about its functionality.
Well, hope you liked it. See you soon and remember, keep reversing. ツ
– fr4mered